Radio or wireless is a way of transmitting energy through empty space, energy carried by invisible waves of electricity and magnetism vibrating through the air at the speed of light. Today, all kinds of things work using the same wireless technology, from digital radio and television to cell phones, and wireless Internet.
Anti-store-burglary devices send radio waves into stores, hoping to catch a stolen book or CD as it passes by. But how do EAS systems actually work?
Imagine that you are tasked with designing an anti-store-burglary device using some old radios you find in your garage. You could build something a bit like a radar (with a combined radio transmitter and receiver), place it in front of a store, and point it at people passing by. Radio waves would be sent from your transmitter, reflected back by the person passing by, and then reflected back to your radio receiver. The problem is that this doesn't actually tell you anything useful, because everyone reflects the radio waves in exactly the same way!
The anti shoplifting device has cracked this problem. In addition to having a transmitter and receiver at the door, every item in the store contains a hidden RF "tag". In bookstores and libraries, you'll find very discreet "soft tags" affixed to one of the pages. In record stores, RF tags may be attached to plastic shrink-wrap, or CDs may be locked in large plastic cases with built-in RF tags that can only be removed with special tools at checkout.
Often, the term "RFID" is used loosely to describe both, but they are very different: RF tags both send the same simple signal that simply tells the receiver something is there; RFID tags send a more complex signal that uniquely identifies whatever they are attached to.
These are the simplest of the RF tags, and they are used primarily for what is called Electronic Article Surveillance (EAS). All tags are identical and none of them can identify the article to which they are attached. So in a store, an RF tag will alert you when you try to steal something, but the alert mechanism doesn't know what you're stealing, only that you're stealing something.
RF tags are sometimes referred to as transponders or chipless RFID tags.
They are more advanced and different from simple RF tags because they uniquely identify the item to which they are attached: the radio signal transmitted from the item to the receiver contains a digitally encoded identifier. That's how library self-checkout machines work: they transmit radio waves to an RFID tag on the back of a book, receive the radio signal from the book, and then decode it to find the digital code that uniquely identifies the book you want. Unlike RF tags, RFID tags tend to work over shorter distances.
EG-AR02 EAS Self Alarm Tag with Lanyard
Imagine a thief trying to steal a book from a store. He doesn't realize that the store is using Electronic Article Surveillance (EAS): the book has an RF tag attached to the back cover. The following is the sequence of steps to trigger the alarm.
The door on one side of the entrance contains a radio transmitter. This continuously transmits radio waves to the door opposite the entrance, which has a radio receiver.
A thief walks through the doorway with a stolen book that contains a hidden RF tag affixed to a label inside that receives radio waves.
Once activated, the RF tag emits its own radio waves at a very precise frequency. The receiver door receives the radio waves and identifies their frequency.
If the frequency is correct, the door will determine that a stolen item is passing through and sound an alarm.
Whatever the future holds, if you are the owner of a store or library and want to prevent thieves from damaging your property, now is the time to contact us to get an EAS system.
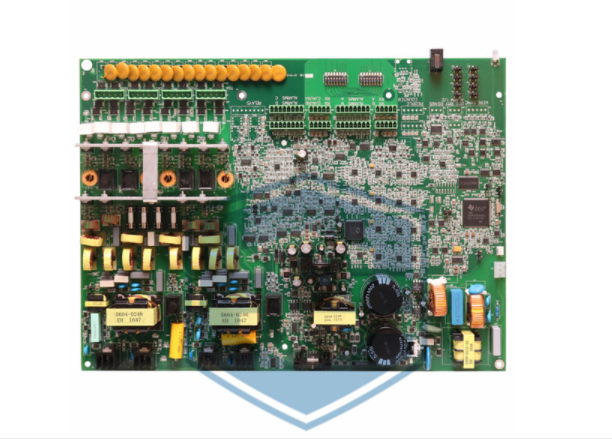
Basic Approach to Preventing Retail Business Losses
Apr. 16, 2022
What You Need to Know about EAS Security Tag Alerts
Apr. 06, 2022